SICTF-Round3#WP
最后更新时间:
Misc:
[签到]签到
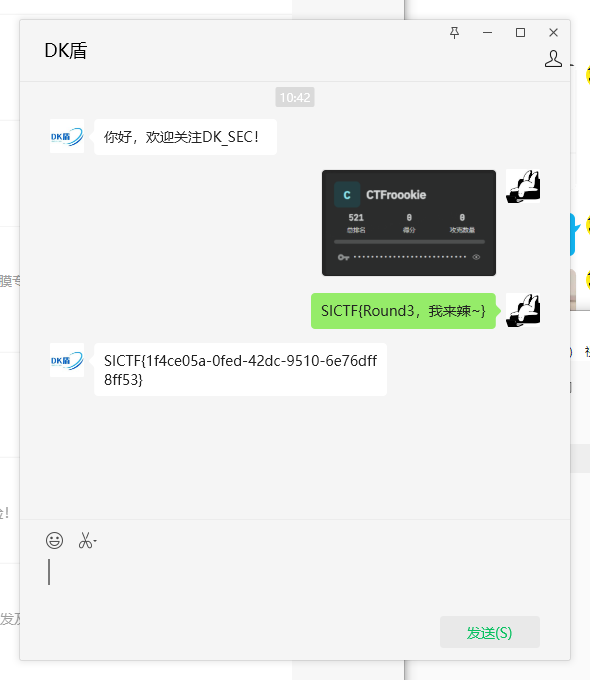
FLAG:SICTF{1f4ce05a-0fed-42dc-9510-6e76dff8ff53}
WHO?WHO?WHO
题目描述:我不说是谁了!!!太渣了!!!呜呜呜!!!让我遍体鳞伤!!!
提示:压缩包密码为6位小写字母,树木是渣男
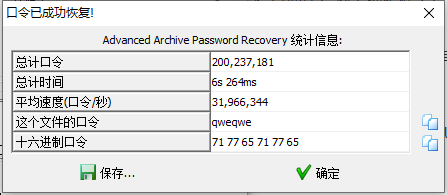
爆破口令解压文件
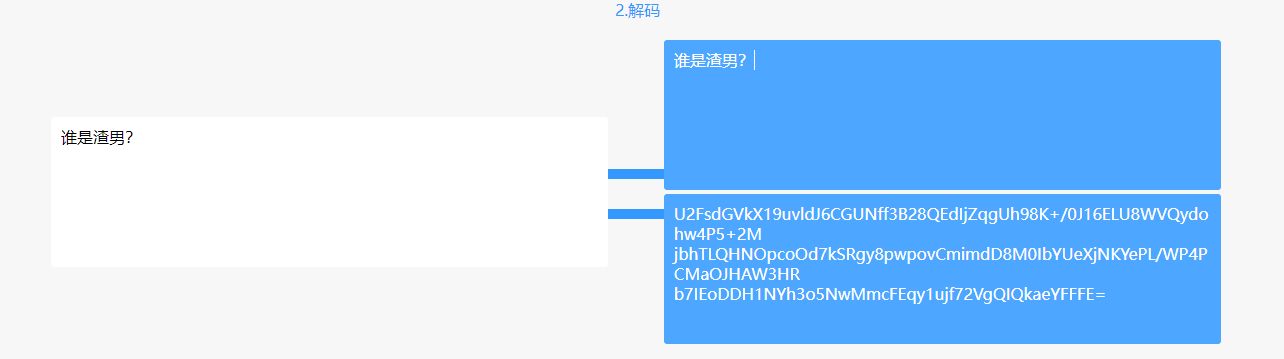
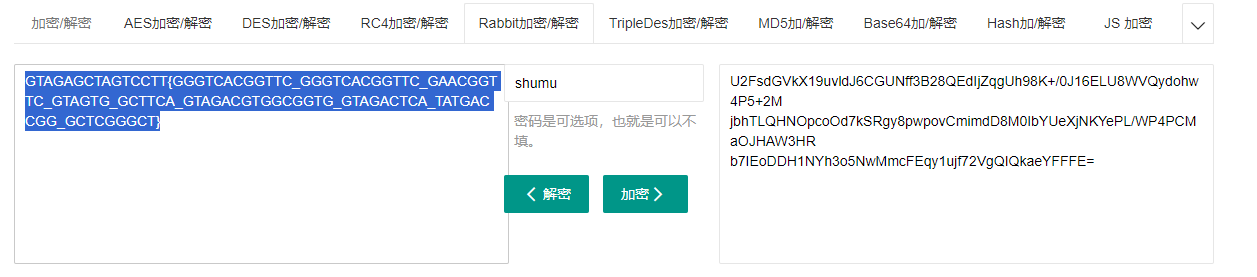
树木的DNA里都是渣男DNA解码,null为_和{}
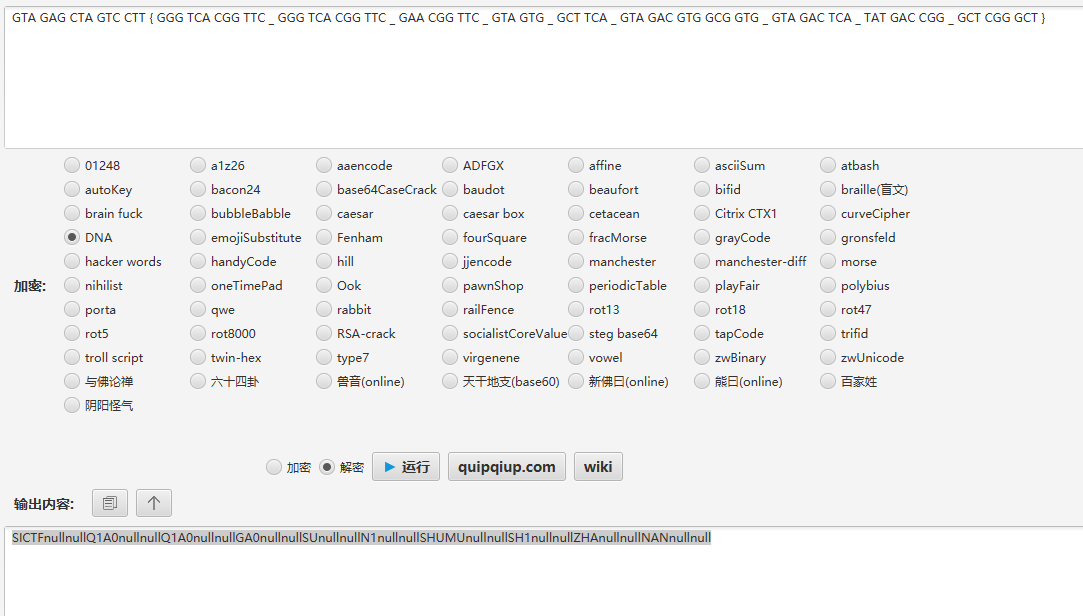
处理一下
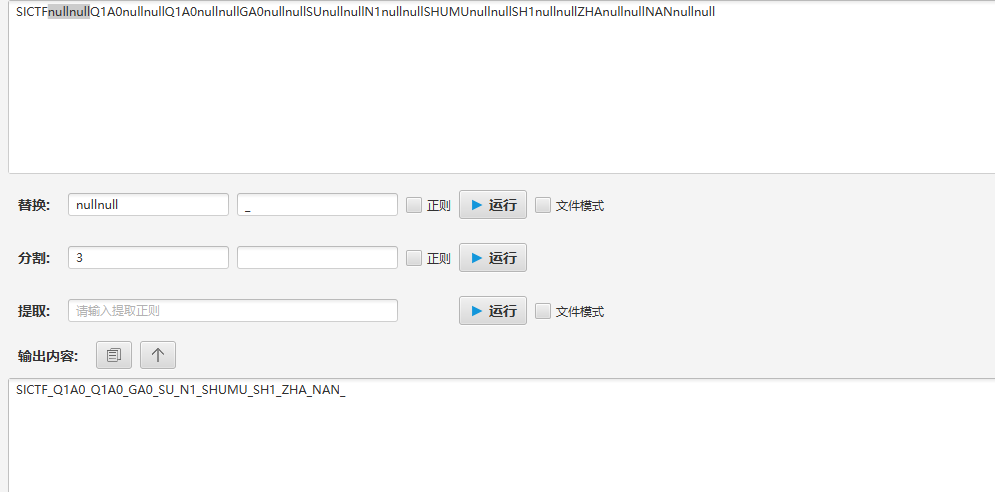
FLAG:SICTF{Q1A0_Q1A0_GA0_SU_N1_SHUMU_SH1_ZHA_NAN}
日志分析1
使用Windows事件查看器导出csv格式文件分析
搜集的线索
1 | 使用者: |
FLAG:SICTF{192.168.222.200|attack$|Administrators|callback|C:\windows\system32\windows_attack.exe|ADOFLMB\attack$}
日志分析2
题目描述:没想到刚刚修复回来的阿帕奇又被入侵了,师傅们速度来揪出树魔王的蛛丝马迹吧!flag格式为 SICTF{攻击者的IP地址|攻击者得到Web应用后台管理权限的方法|攻击者在SQL注入攻击过程中使用的自动化工具名称|工具版本号|攻击者使用的Webshell连接工具(中文名)|工具版本号}
2198行和45860行
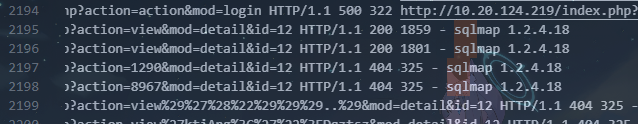
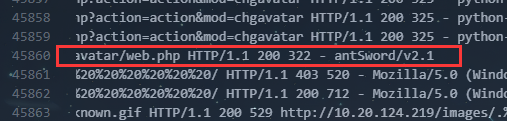
FLAG:SICTF{10.11.35.95|暴力破解|sqlmap|1.2.4.18|蚁剑|2.1}
神秘流量
提示:你听说过CS吗?
根据提示我搜到了Cobalt Strike 网络流量,首先把流量包内的dmp.zip压缩包提取出来解压备用
尝试提取加密数据流量:
1 | ┌──(kali㉿kali)-[~/Desktop/Beta-master] |
尝试提取密钥:
1 | ┌──(kali㉿kali)-[~/Desktop/Beta-master] |
之后就可以使用提取的 AES 和 HMAC 密钥解密流量(-k HMACkey:AESkey):
1 | ┌──(kali㉿kali)-[~/Desktop/Beta-master] |
FLAG:SICTF{b50936c7-b60d-411e-a91f-304937164b9c}
问卷调查
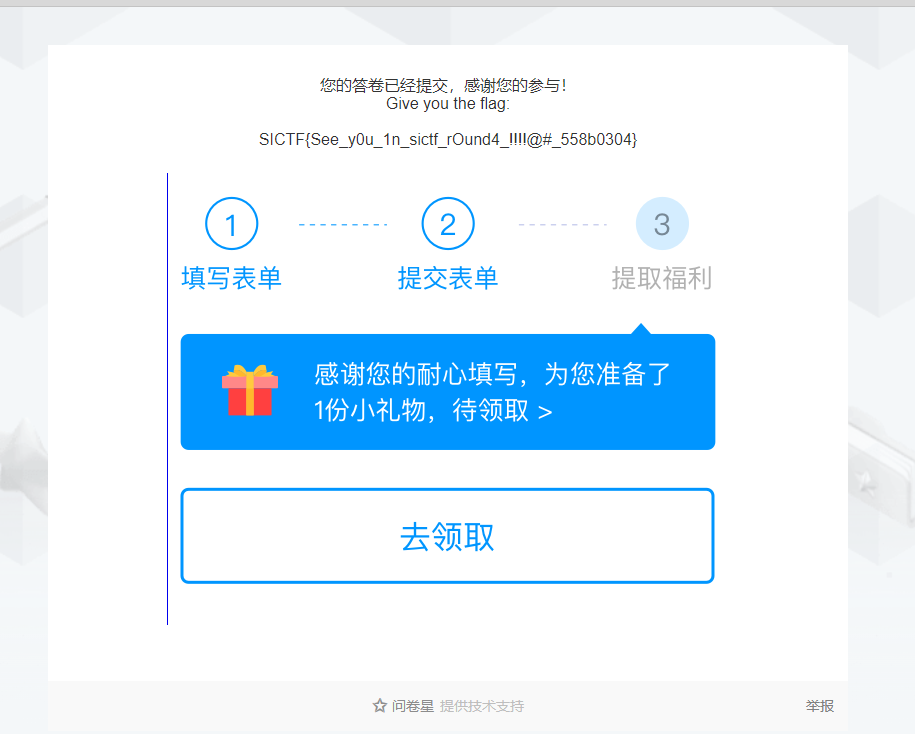
FLAG:SICTF{See_y0u_1n_sictf_rOund4_!!!!@#_558b0304}
Crypto:
[签到]Vigenere
在线网站直接破解
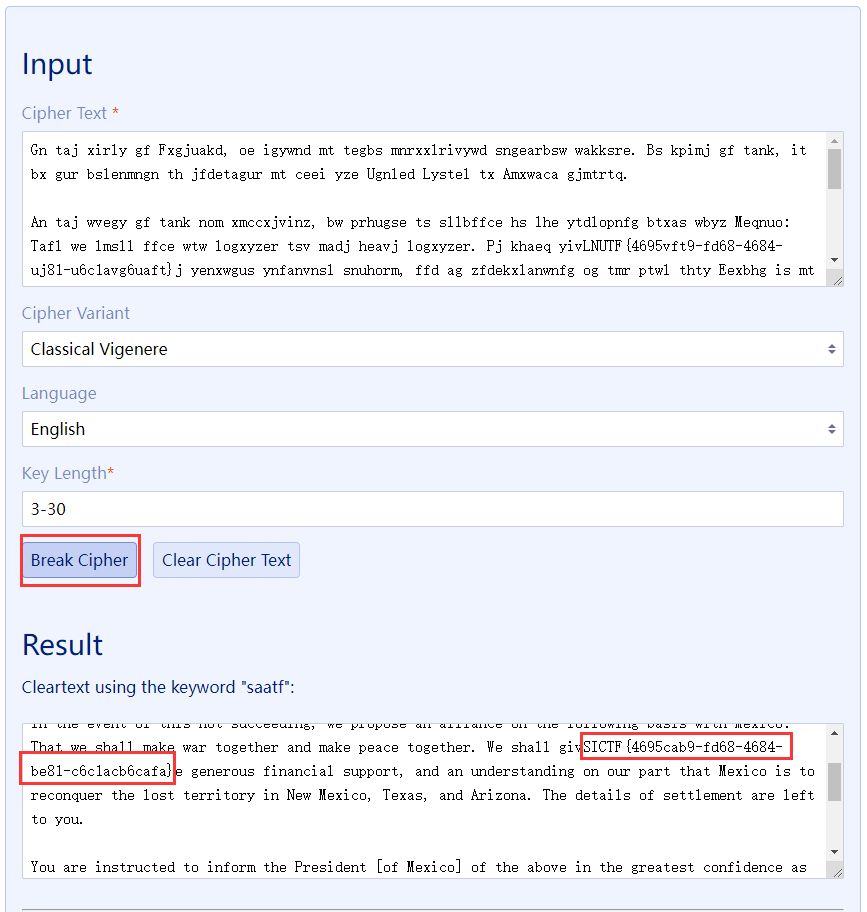
FLAG:SICTF{4695cab9-fd68-4684-be81-c6c1acb6cafa}
Reverse:
[签到]Baby_C++
1 |
|
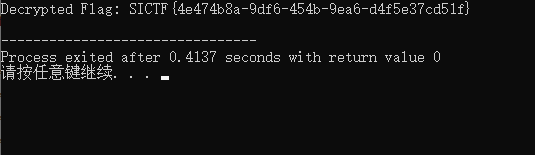
FLAG:SICTF{4e474b8a-9df6-454b-9ea6-d4f5e37cd51f}
[Game][Battle City]
游戏通关就给flag在assets文件夹内win.png
由于我太菜了,所以使用了外挂变速,这样我就能反应过来了
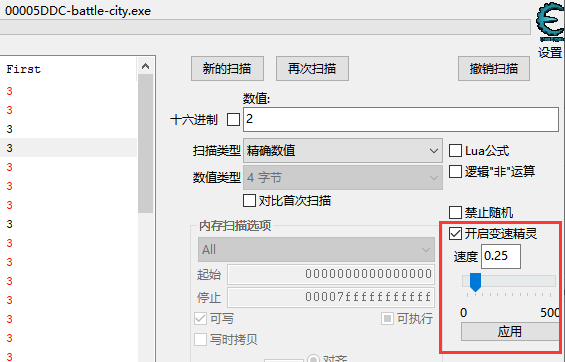
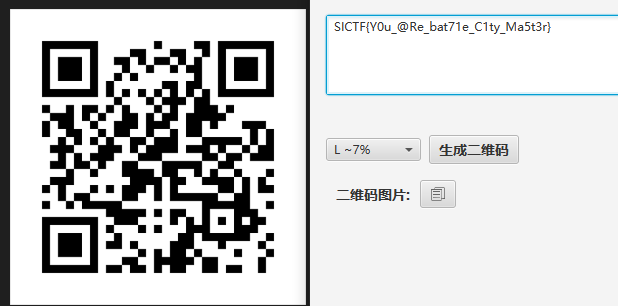
FLAG:SICTF{Y0u_@Re_bat71e_C1ty_Ma5t3r}
Forensics:
[签到]OSINT签到
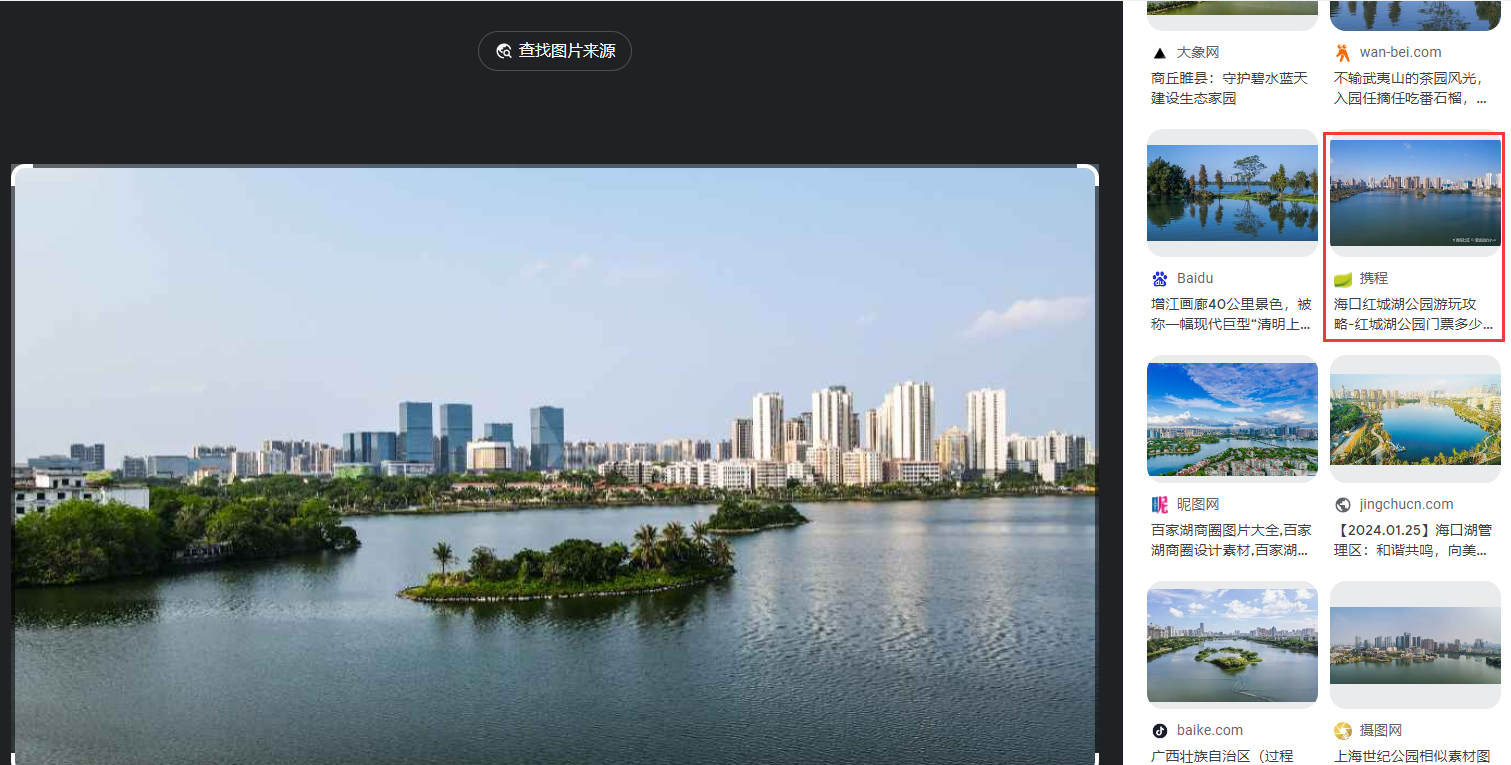
FLAG:SICTF{海南省_海口市_琼山区_红城湖公园}
这才是签到
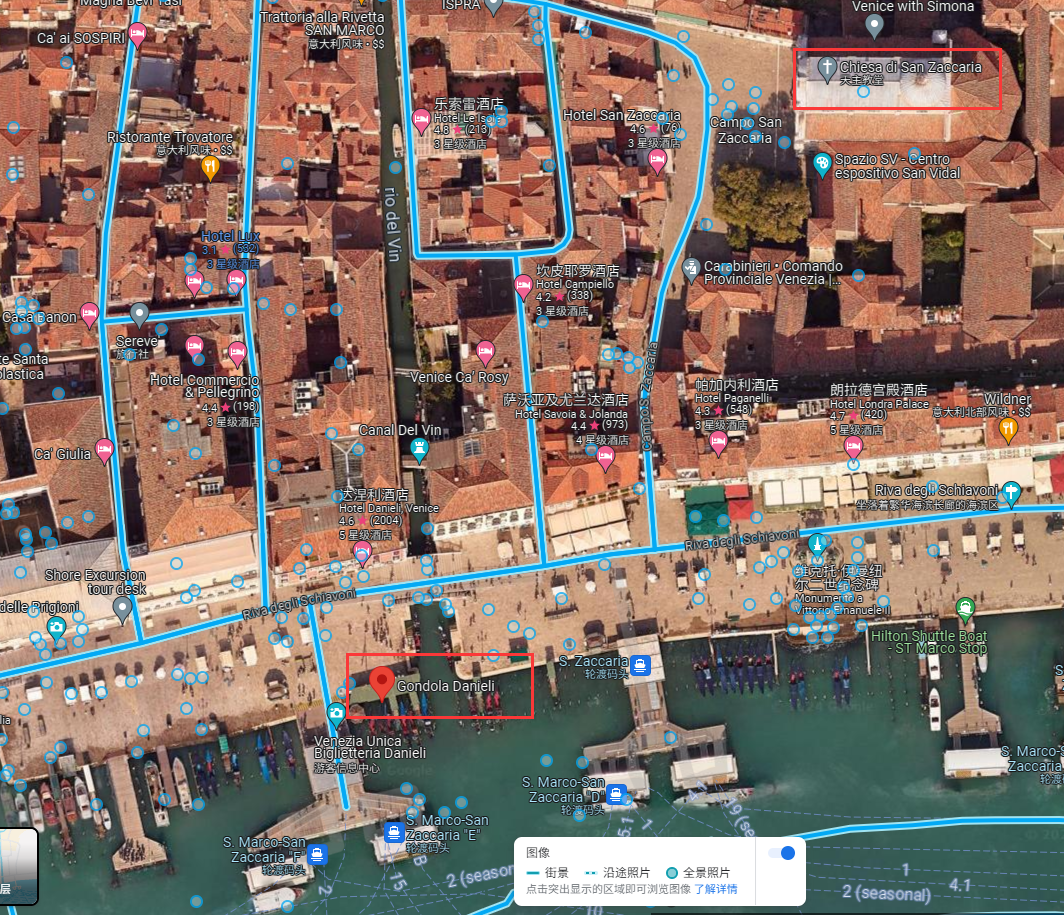
FLAG:SICTF{意大利_威尼斯_GondolaDanieli_ChiesadiSanZaccaria}
树木的压迫
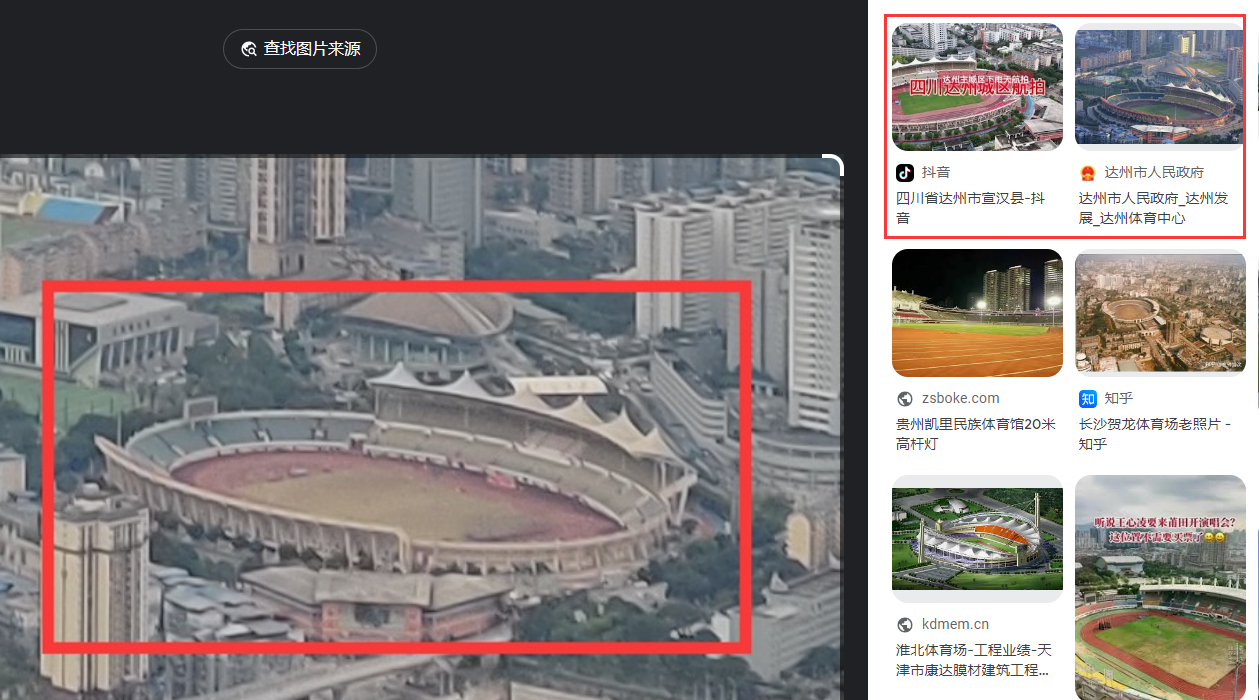
FLAG:SICTF{四川省_达州市_通川区_凤凰大道376号_达州市体育中心}
真的签到
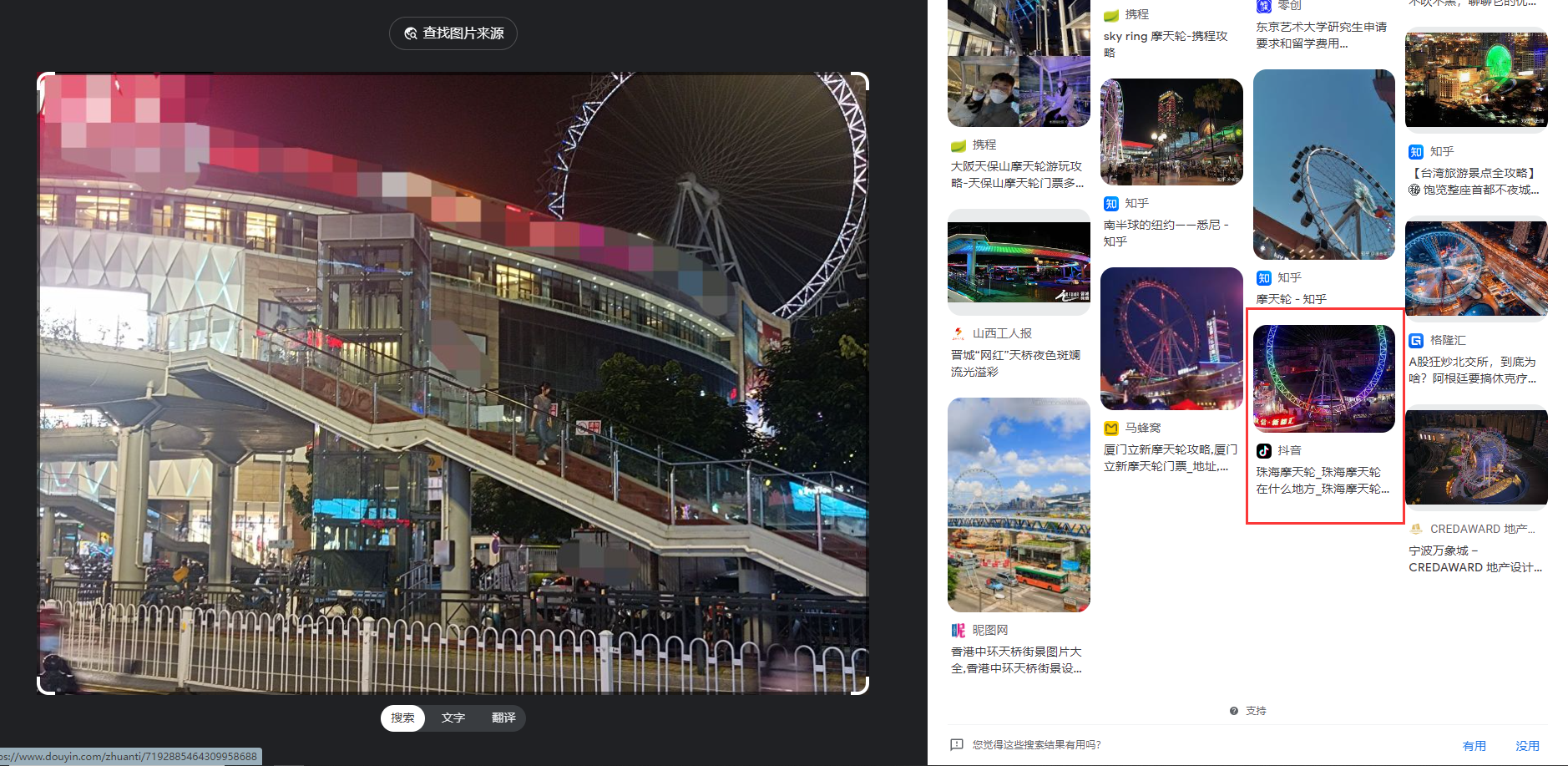
FLAG:SICTF{广东省_珠海市_斗门区_大信新都汇}
签退
看到后面的蜘蛛侠到谷歌识图找到地址

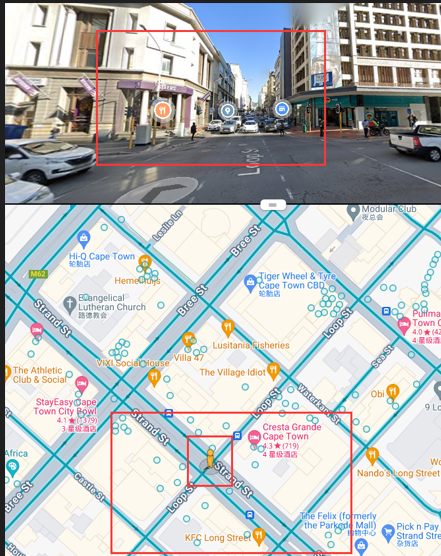
FLAG:SICTF{南非_开普敦_StrandSt_STEERS}